Author: Tommy Hartono
-
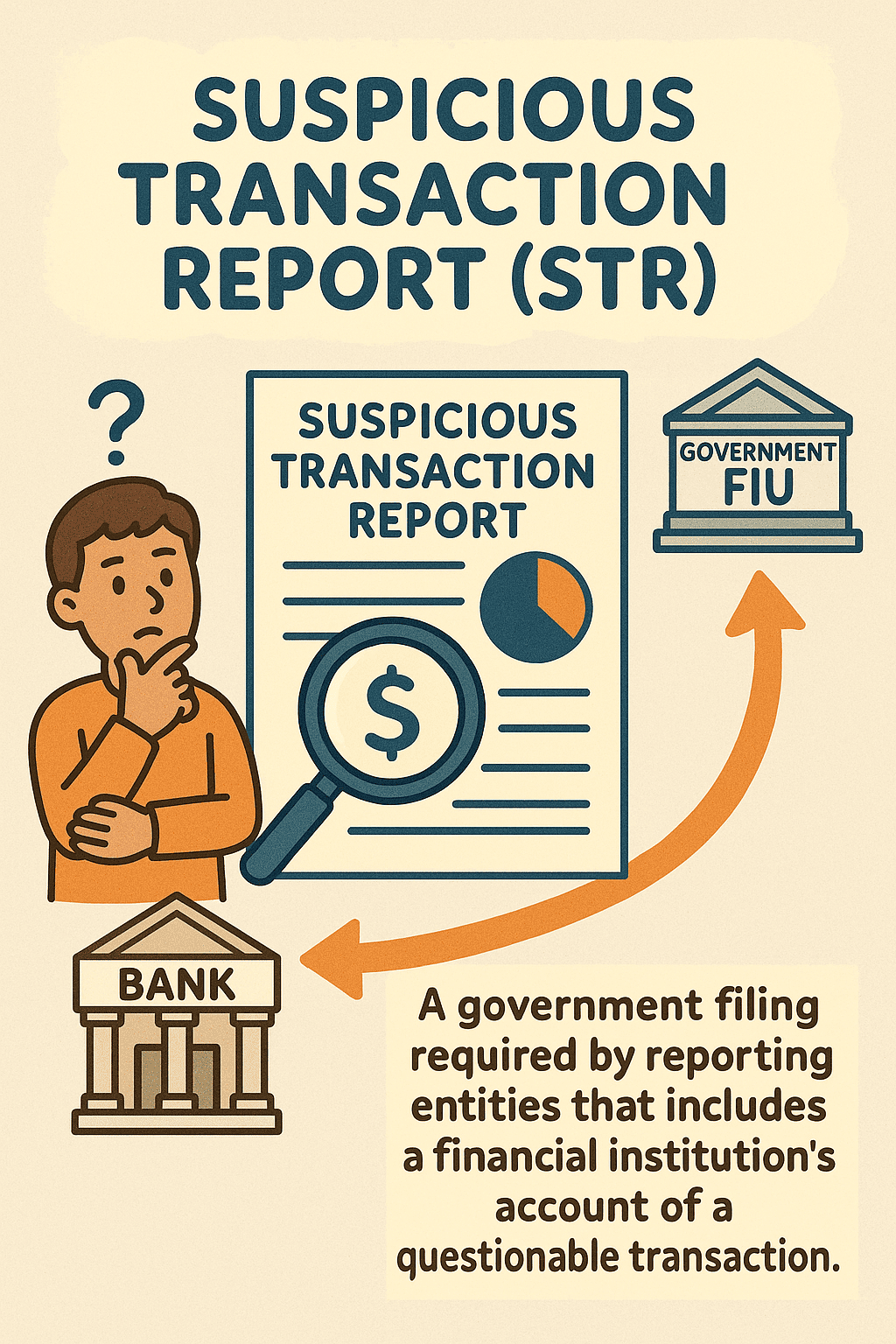
Day 262: Suspicious Transaction Report
The post discusses tactics used by criminals to launder money, such as fake businesses and structuring deposits. It highlights the importance of Suspicious Transaction Reports (STRs) in detecting these activities. Through advanced technology and collaboration, financial institutions can effectively combat money laundering and protect assets. STRs empower banks to act as safeguards.
-
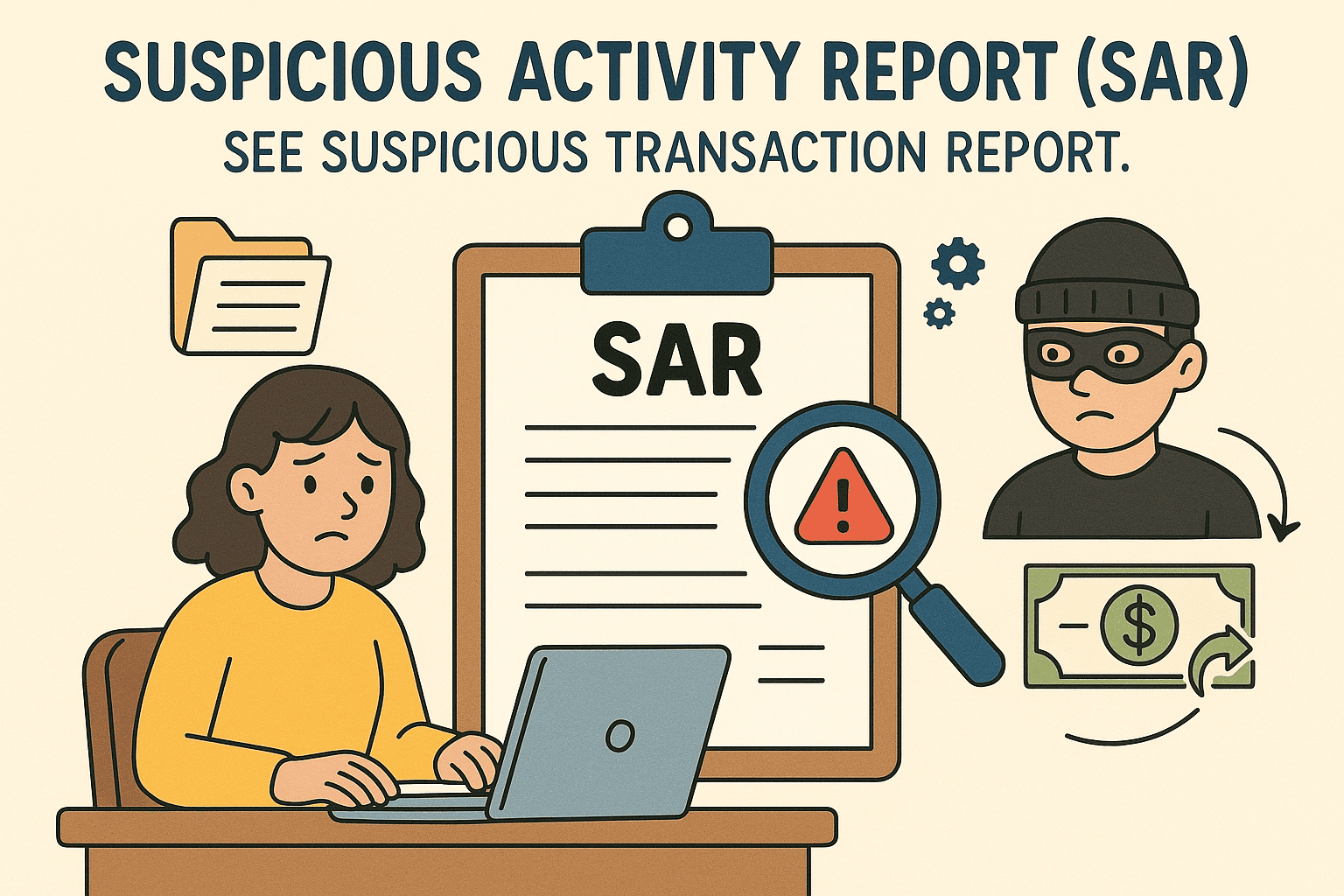
Day 261: Suspicious Activity Report
Banks combat financial crime by identifying tactics used by criminals, such as structuring large sums into smaller deposits, fake businesses, money laundering, and identity theft. In 2023, banks filed 4.6 million Suspicious Activity Reports, utilizing advanced technology to efficiently analyze transactions and prevent illegal activities while ensuring compliance.
-
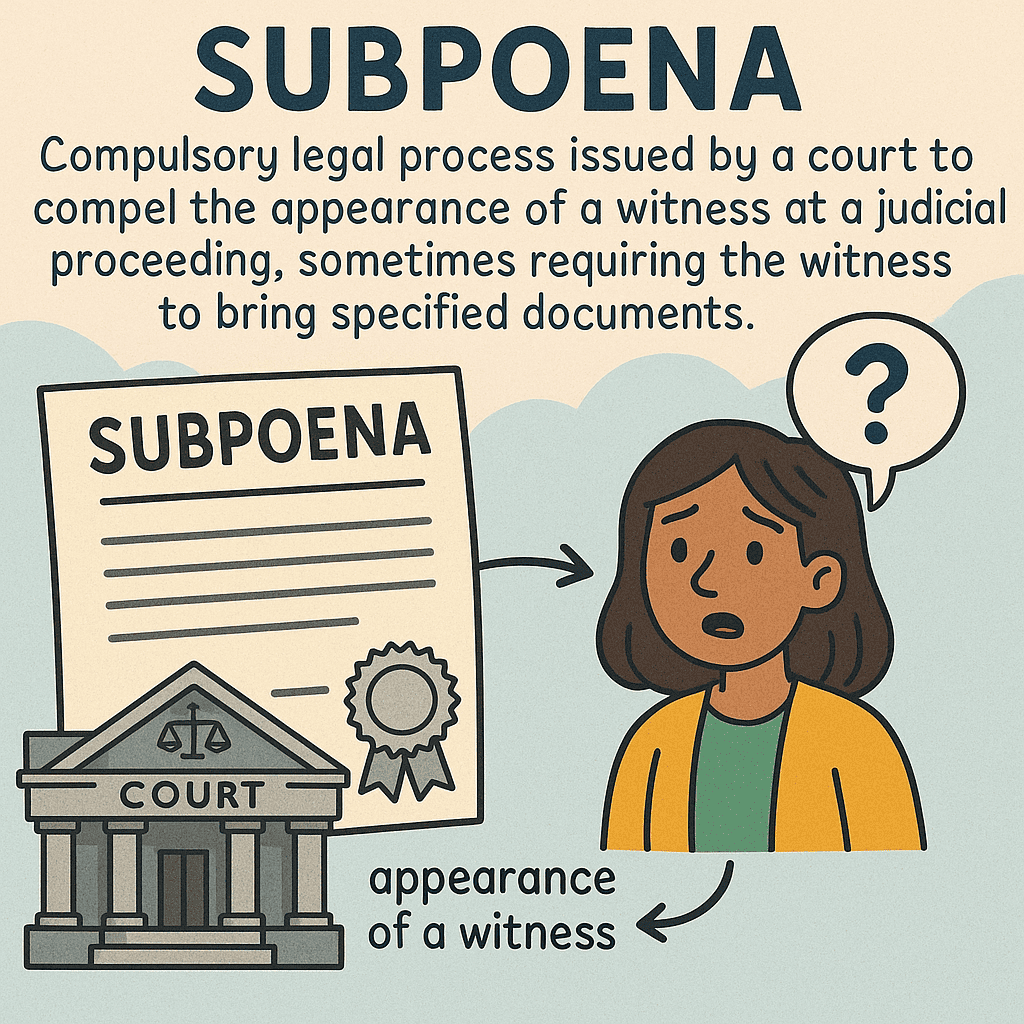
Day 259: Subpoena
Subpoenas serve as crucial legal tools in uncovering financial crimes, yet criminals exploit them to hinder investigations. Techniques like “structuring,” shell companies, and anonymous crypto wallets complicate law enforcement efforts. However, advancements in technology, including AI and open-source tools, are enhancing capabilities to combat these tactics effectively.
-
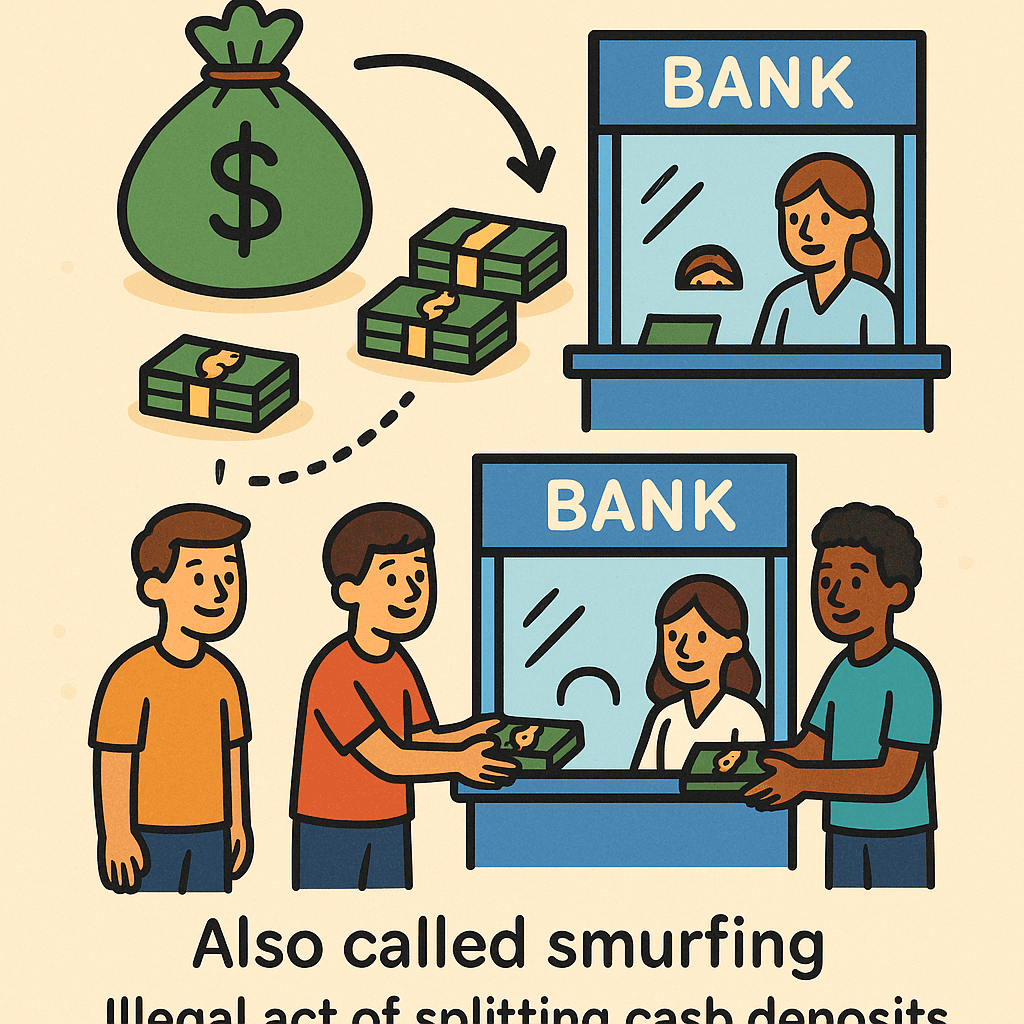
Day 258: Structuring
Criminals use “Structuring” or “Smurfing” to launder money by breaking large amounts into smaller deposits to avoid detection. For instance, a drug dealer deposits $50,000 as five $9,999 transactions. This technique aids crimes and risks financial integrity. However, technology like Mulai Console is enhancing banks’ ability to combat such activities.
-
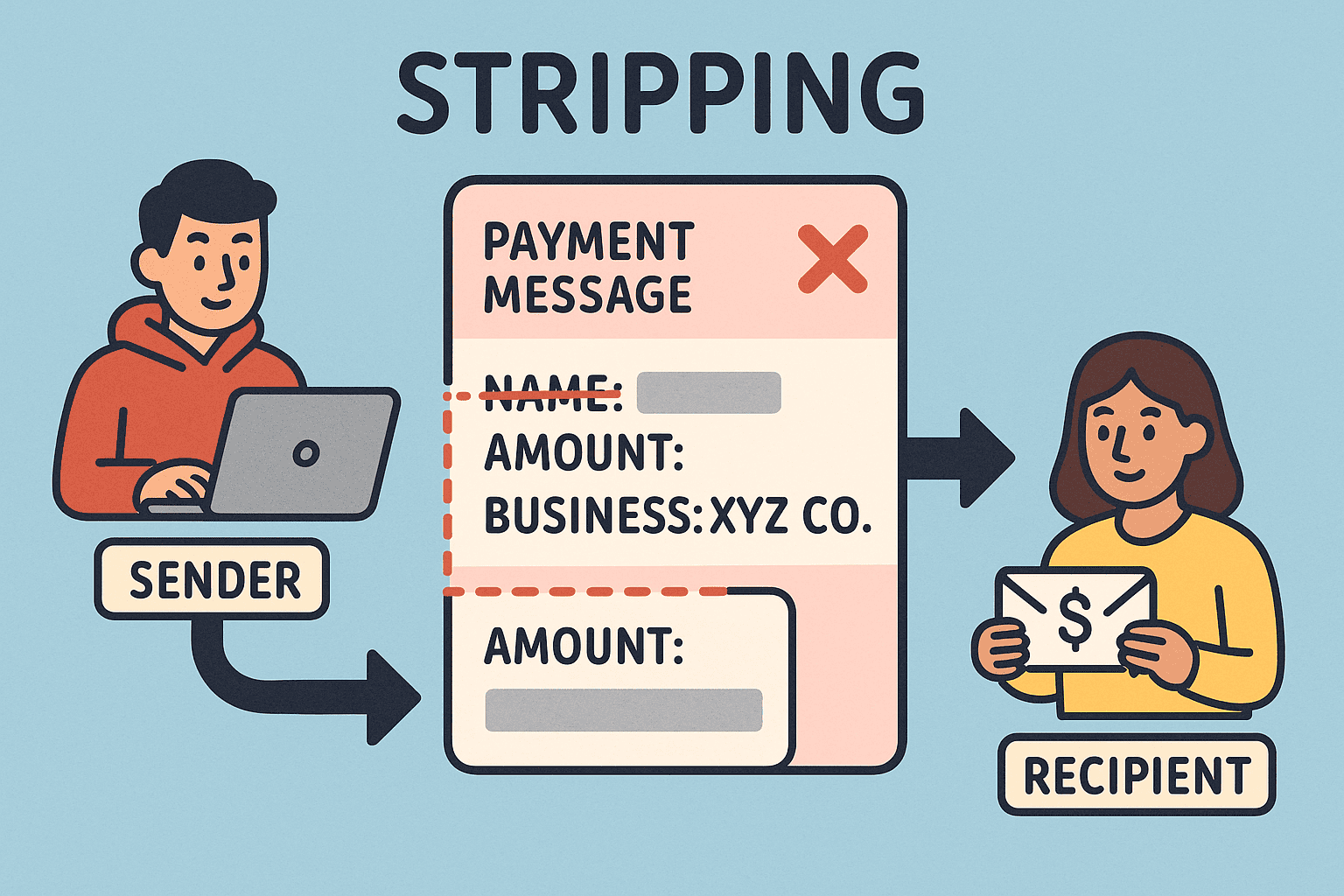
Day 257: Stripping
The “Invisible Money” Trick, known as “Stripping,” allows criminals to obscure the source of illicit funds by altering transaction details. This technique facilitates money laundering, affecting banks globally and increasing costs for consumers. Innovative technologies and collaborative regulations are emerging to combat these practices and enhance financial transparency.
-
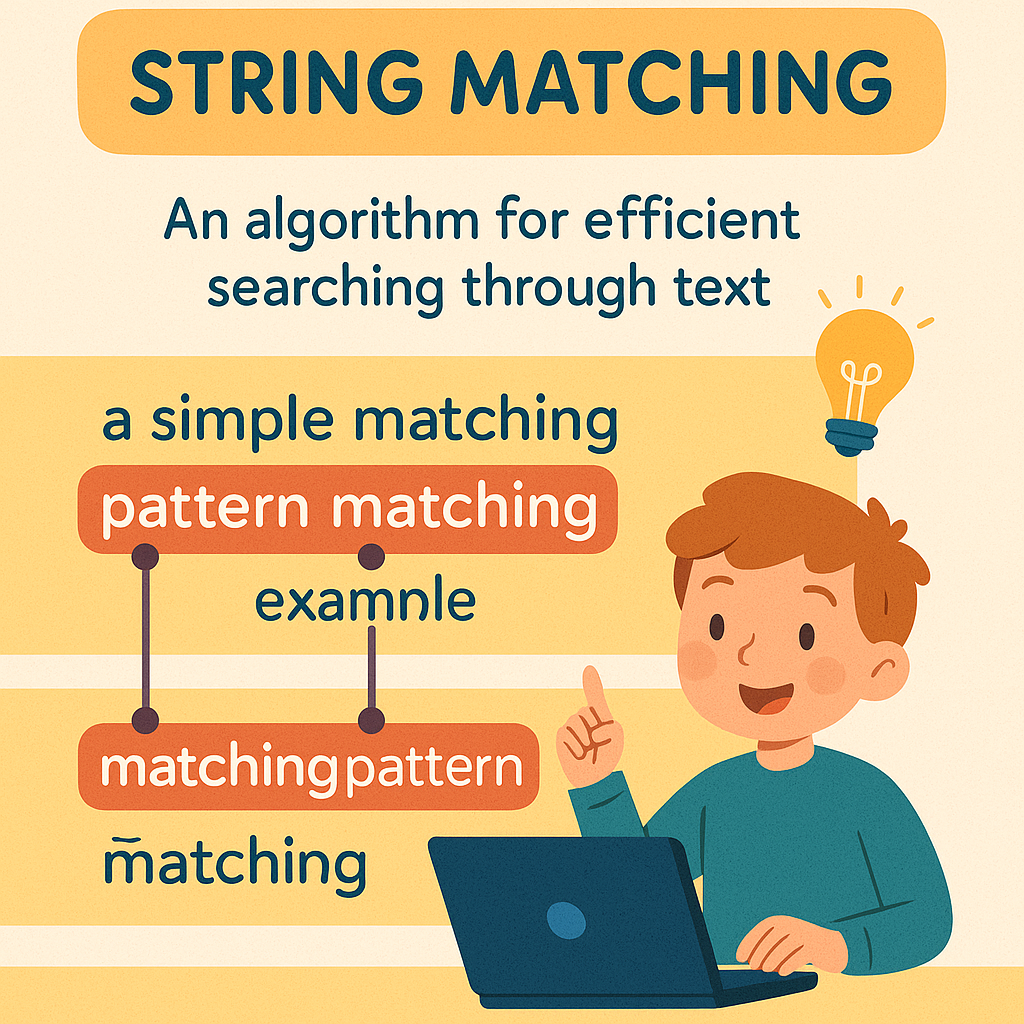
Day 256: String Matching
Financial criminals utilize name, number, and code alterations to evade detection, leading to challenges for traditional security systems. Advanced methods like fuzzy matching and analyzing behavioral data enhance fraud detection. By adopting inclusive technologies and shared innovations, we adapt to evolving tactics and improve our defenses against financial crime.
-

Day 255: Strict Liability
Strict liability in sanctions compliance punishes companies for others’ mistakes, allowing criminals to exploit gaps. Tactics include using fake owners, minor invoice errors, and hiding within legitimate businesses to evade fines. To combat this, technology like inclusive regtech can enhance detection of hidden risks, making financial crimes harder to conceal.
-
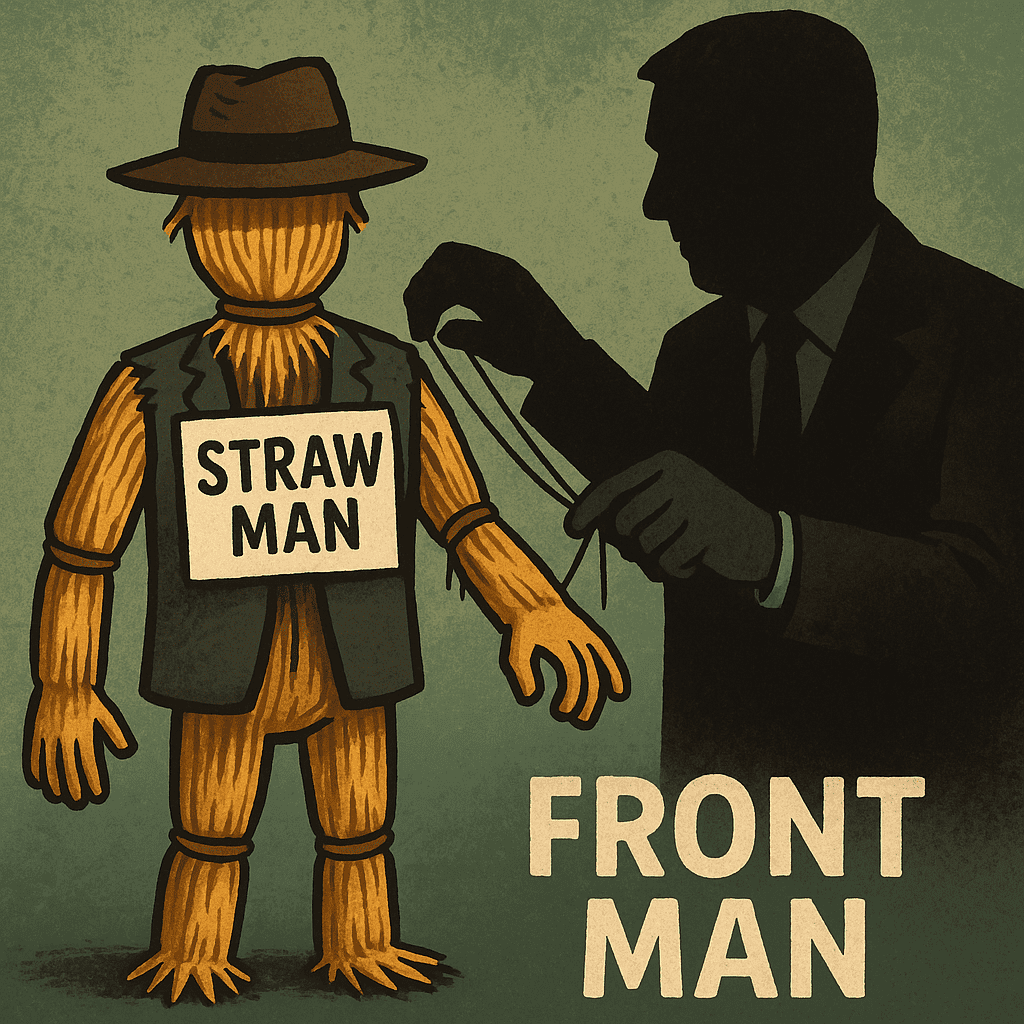
Day 254: Straw Men
#QuickbiteCompliance day 254 🚨 The Puppet Show: How Straw Men Hide Sanctioned Criminals Imagine your friend is banned from the candy store but secretly pays you to buy sweets for them. You’re the “puppet” (aka Straw Man)—acting for someone who’s hiding in the shadows. Here’s how criminals use these puppets to cheat the system: —…
-

Day 253: Sting Operation
#QuickbiteCompliance day 253 🔍 Ever Played “Cops and Robbers”? Real-Life Cops Use “Make-Believe” to Catch Bad Guys! Imagine a police officer dressing up as a watch seller 🕰️, a wedding planner 💒, or even a hacker 💻 to trick criminals into showing their secrets. That’s a “sting operation”! Law enforcement sets up fake businesses (like…
-

Day 252: SDN List
#QuickbiteCompliance day 252 🔍 The SDN List: Your Guide to Fighting Bad Guys Imagine your school has a “no-trade lunchbox” list. If someone steals snacks, they go on the list—and nobody can trade with them. The SDN List works like that for the U.S. government. It’s a list of people, companies, or groups (like terrorists…
