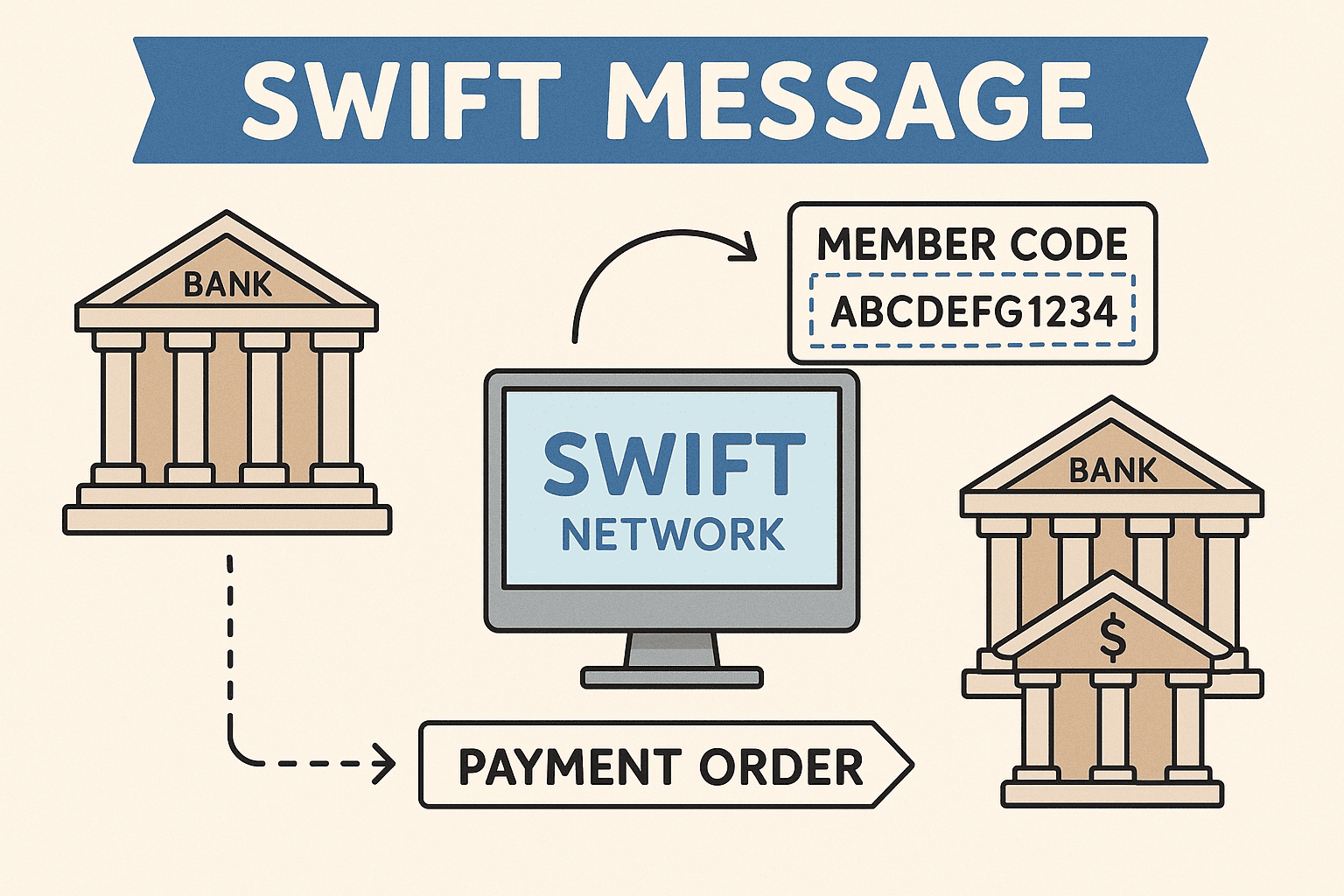
Category: Terms
-
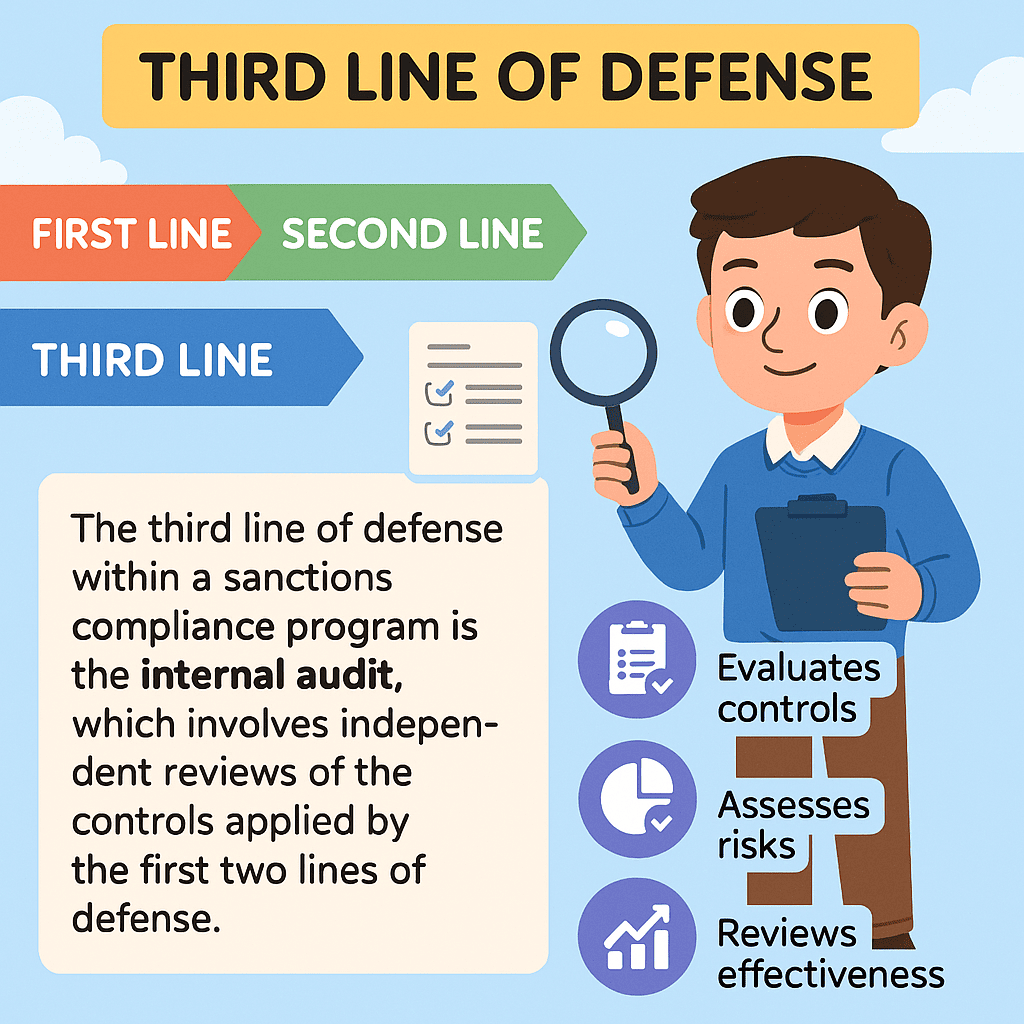
Day 269: Third Line of Defense
Strong audits are crucial in preventing financial crimes at banks, acting as a third line of defense after frontline teams and compliance experts. Weak inspections lead to significant losses, as seen in cases like Entain and TD Bank. Enhancing training, testing controls, and utilizing technology can fortify audit effectiveness against criminals.
-

Day 268: Testimony
Testimony in court can be manipulated by criminals to disguise financial crimes. They employ various tactics, such as paying corrupt experts, utilizing family members for cover-ups, or fabricating business profits. To combat this, technology like AI monitors can detect suspicious patterns, supporting justice by transforming testimony into a protective tool against crime.
-

Day 267: Terrorist Financing
Terrorist groups fund their operations through two main methods: receiving secret donations from supportive individuals or organizations and engaging in illegal activities like drug trafficking and scams. Strategies to combat these financing methods include utilizing technology, global cooperation, and awareness. Disrupting their cash flow is crucial to saving lives.
-
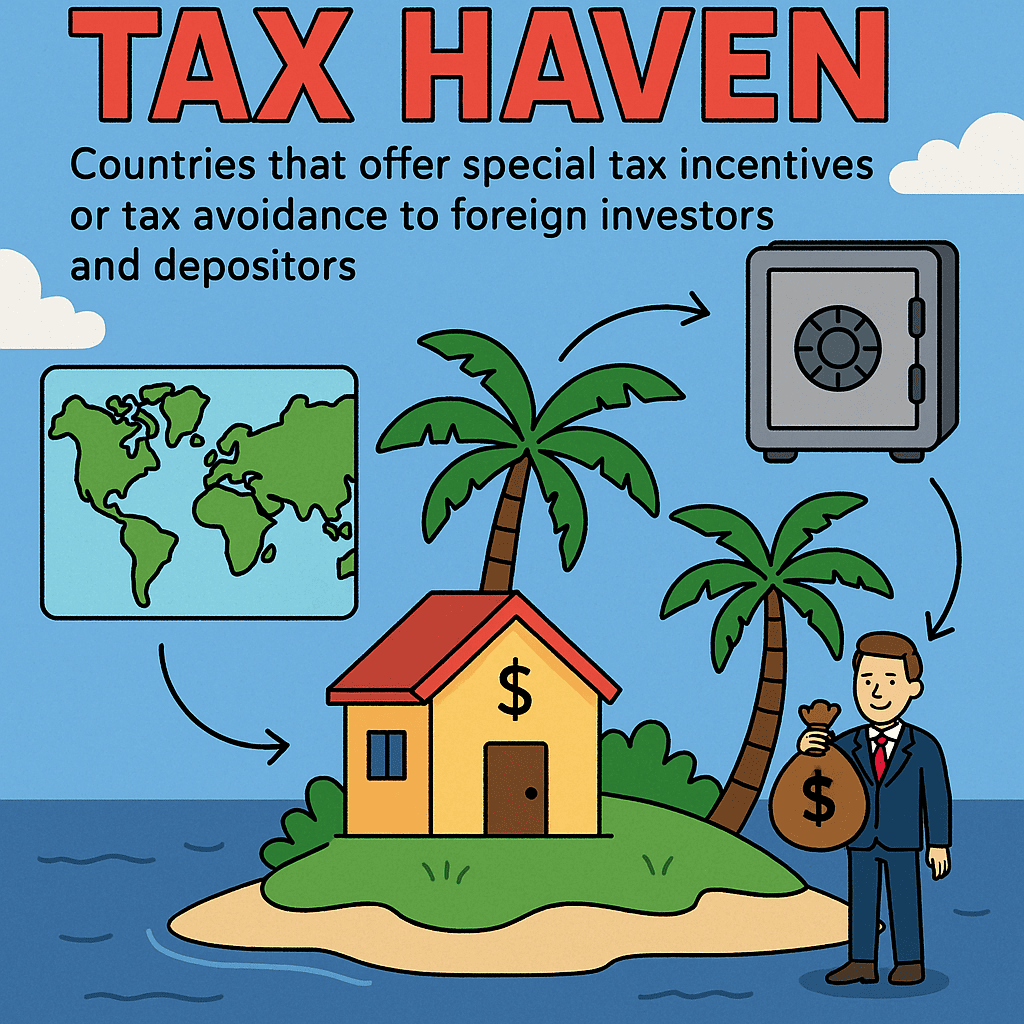
Day 266: Tax Haven
Tax havens, while legal for tax avoidance, are exploited by criminals for money laundering through ghost companies, fraudulent trade invoices, and anonymous trusts. This not only deprives governments of tax revenue, impacting schools and hospitals, but also enables war criminals to hide illicit funds. New regulations aim to improve transparency and combat financial crime.
-

Day 265: Targeted Sanctions
Targeted sanctions aim to punish criminals without impacting innocent citizens, much like banning a single cheating student. However, criminals evade these sanctions through ghost companies, family fronts, and cryptocurrency. Utilizing AI, global cooperation, and public shaming, efforts are made to combat financial crime and ensure accountability.
-
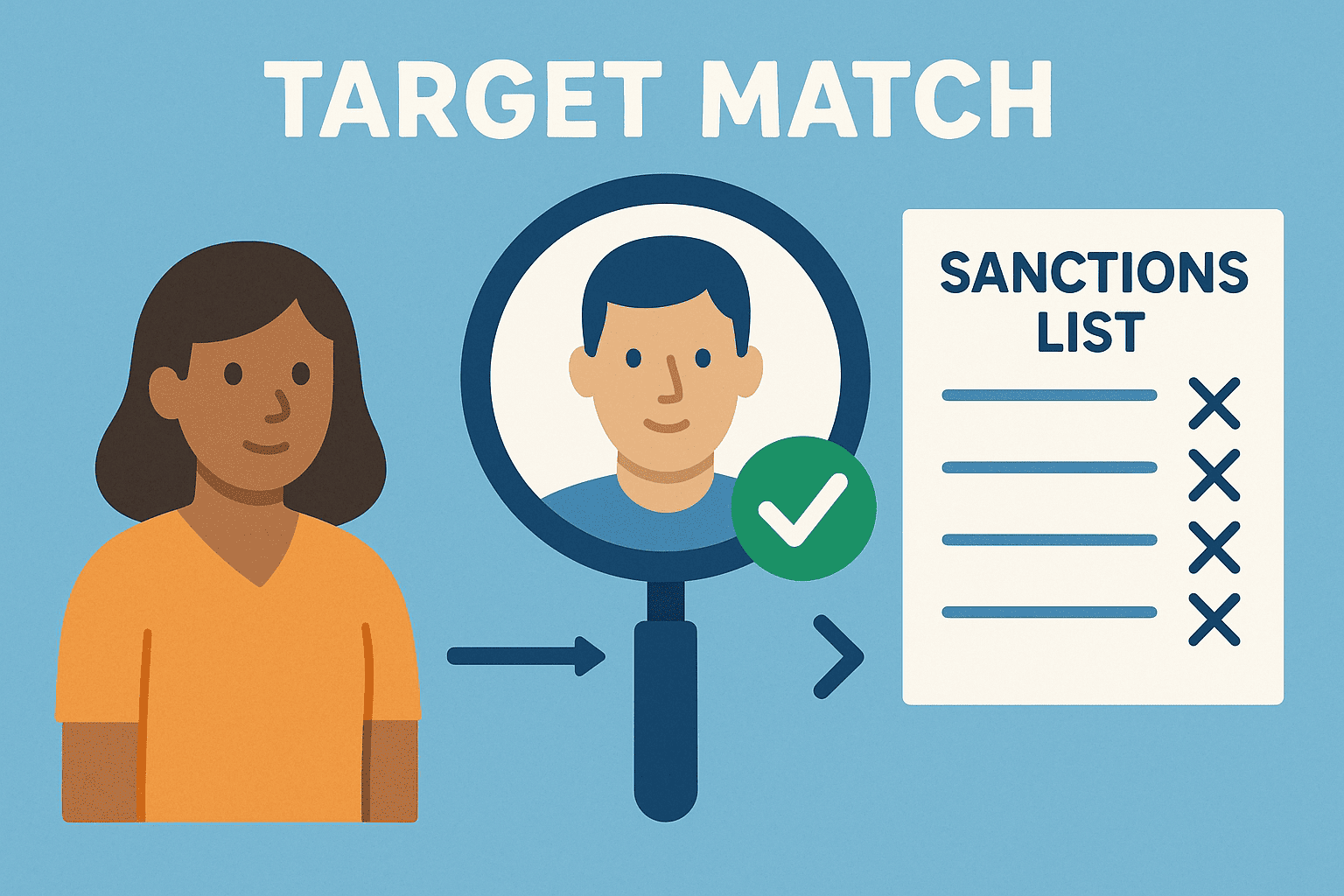
Day 264: Target Match
A Target Match identifies financial criminals attempting to infiltrate the system by matching them against global watchlists. Criminals use tactics like smurfing, shell companies, and name variations to evade detection. Effective screening technology, including AI, can reduce false alarms and improve compliance in fighting money laundering and financial crime.
-
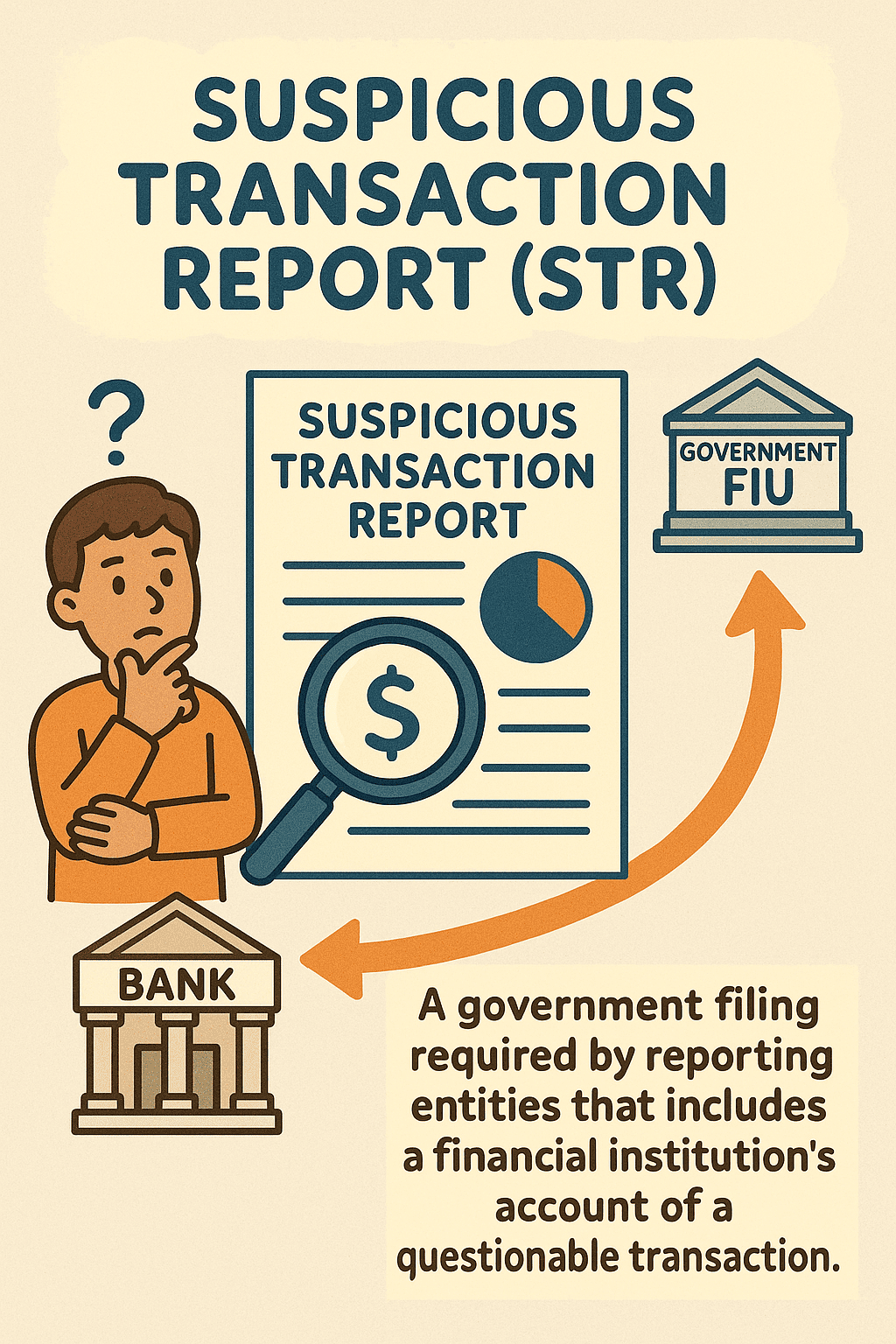
Day 262: Suspicious Transaction Report
The post discusses tactics used by criminals to launder money, such as fake businesses and structuring deposits. It highlights the importance of Suspicious Transaction Reports (STRs) in detecting these activities. Through advanced technology and collaboration, financial institutions can effectively combat money laundering and protect assets. STRs empower banks to act as safeguards.
-
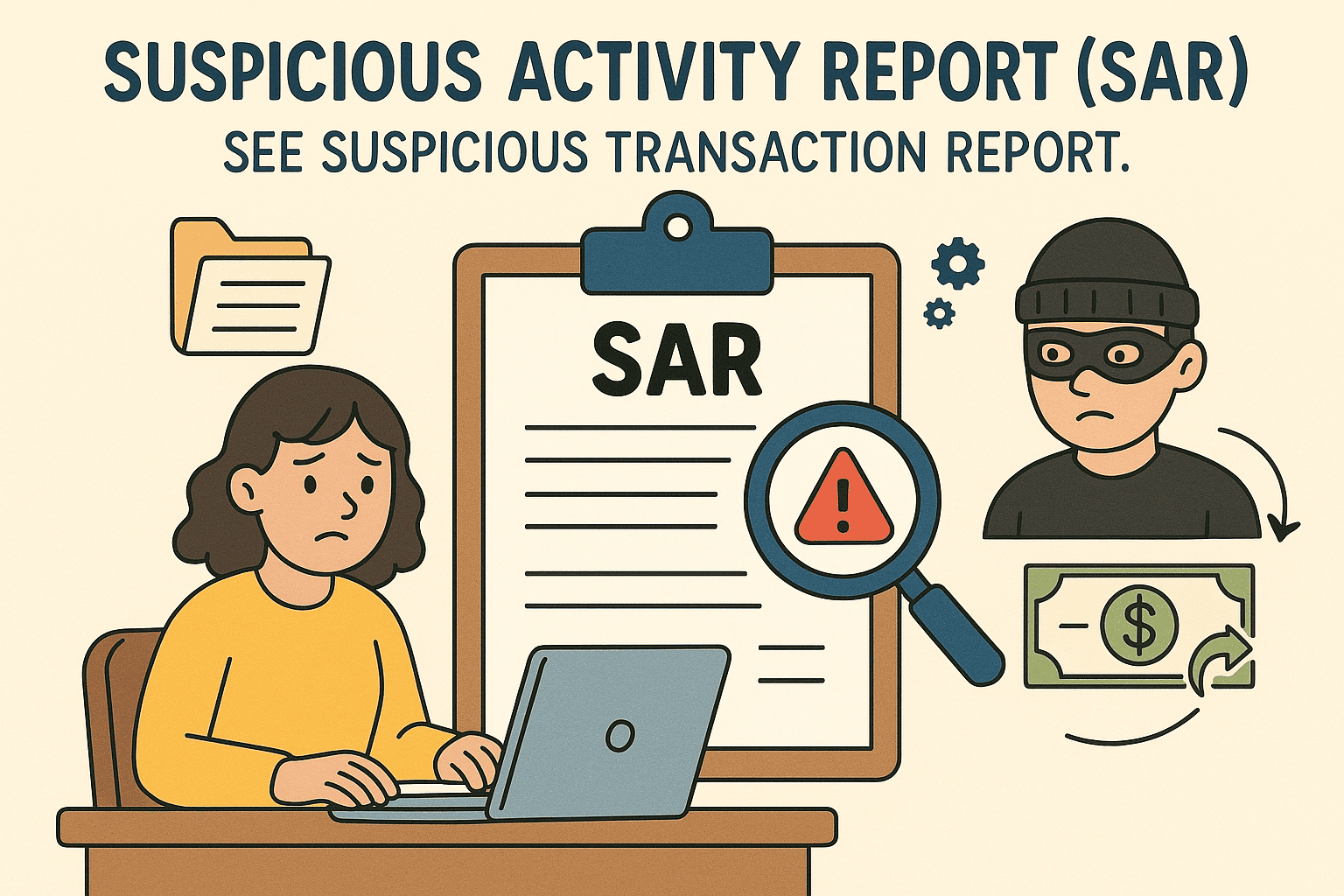
Day 261: Suspicious Activity Report
Banks combat financial crime by identifying tactics used by criminals, such as structuring large sums into smaller deposits, fake businesses, money laundering, and identity theft. In 2023, banks filed 4.6 million Suspicious Activity Reports, utilizing advanced technology to efficiently analyze transactions and prevent illegal activities while ensuring compliance.
-
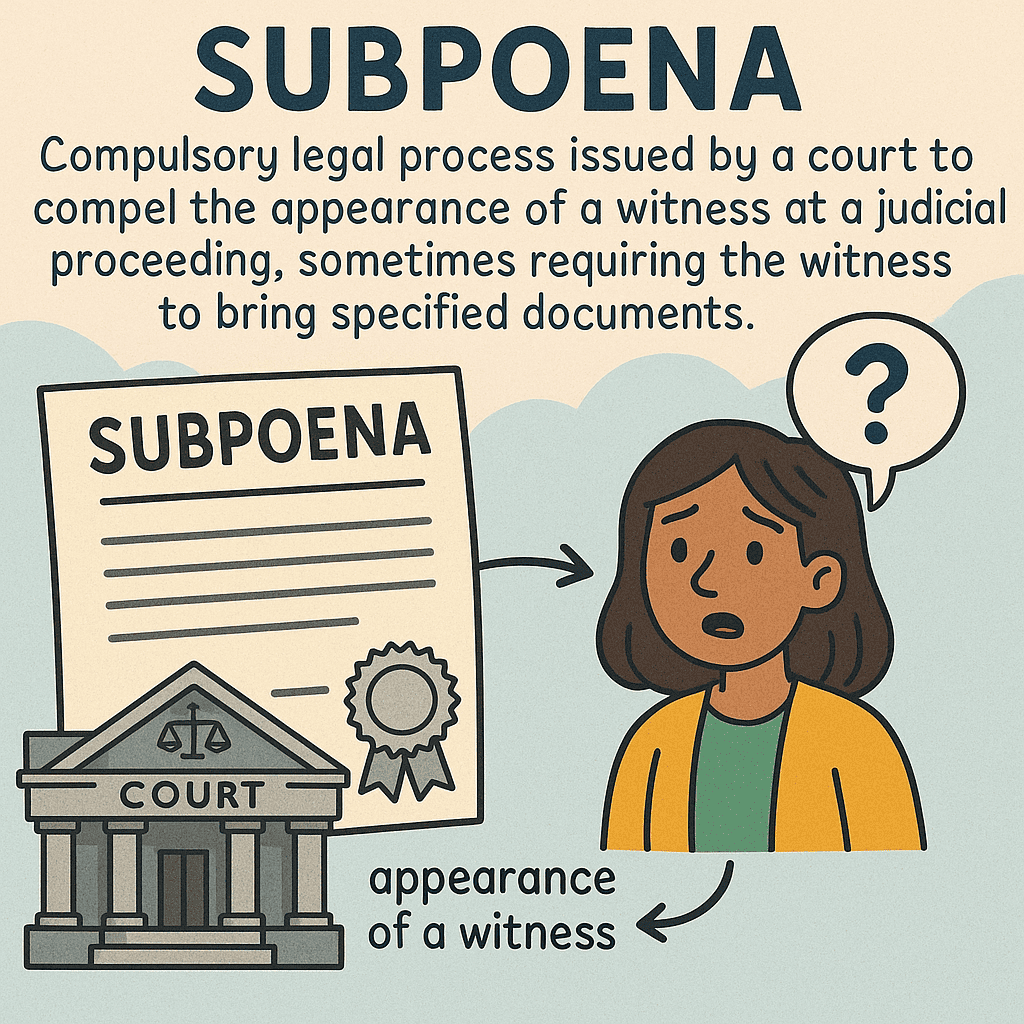
Day 259: Subpoena
Subpoenas serve as crucial legal tools in uncovering financial crimes, yet criminals exploit them to hinder investigations. Techniques like “structuring,” shell companies, and anonymous crypto wallets complicate law enforcement efforts. However, advancements in technology, including AI and open-source tools, are enhancing capabilities to combat these tactics effectively.