
by Tommy Hartono | Jul 31, 2025 | Terms
#QuickbiteCompliance day 285 🚨 How Terrorist Financiers Turn Global Rules Into Loopholes: The UNSCR 1373 Blind Spots UN Security Council Resolution 1373 (2001) was a landmark move to unify countries against terrorism. It mandated all nations...

by Tommy Hartono | Jul 30, 2025 | Terms
#QuickbiteCompliance day 284 How Criminals Exploit Global Systems & How the UN Fights Back As the world grapples with sophisticated financial crime, the United Nations —founded to uphold peace and collective security—plays a pivotal role in...
by Tommy Hartono | Jul 29, 2025 | Terms
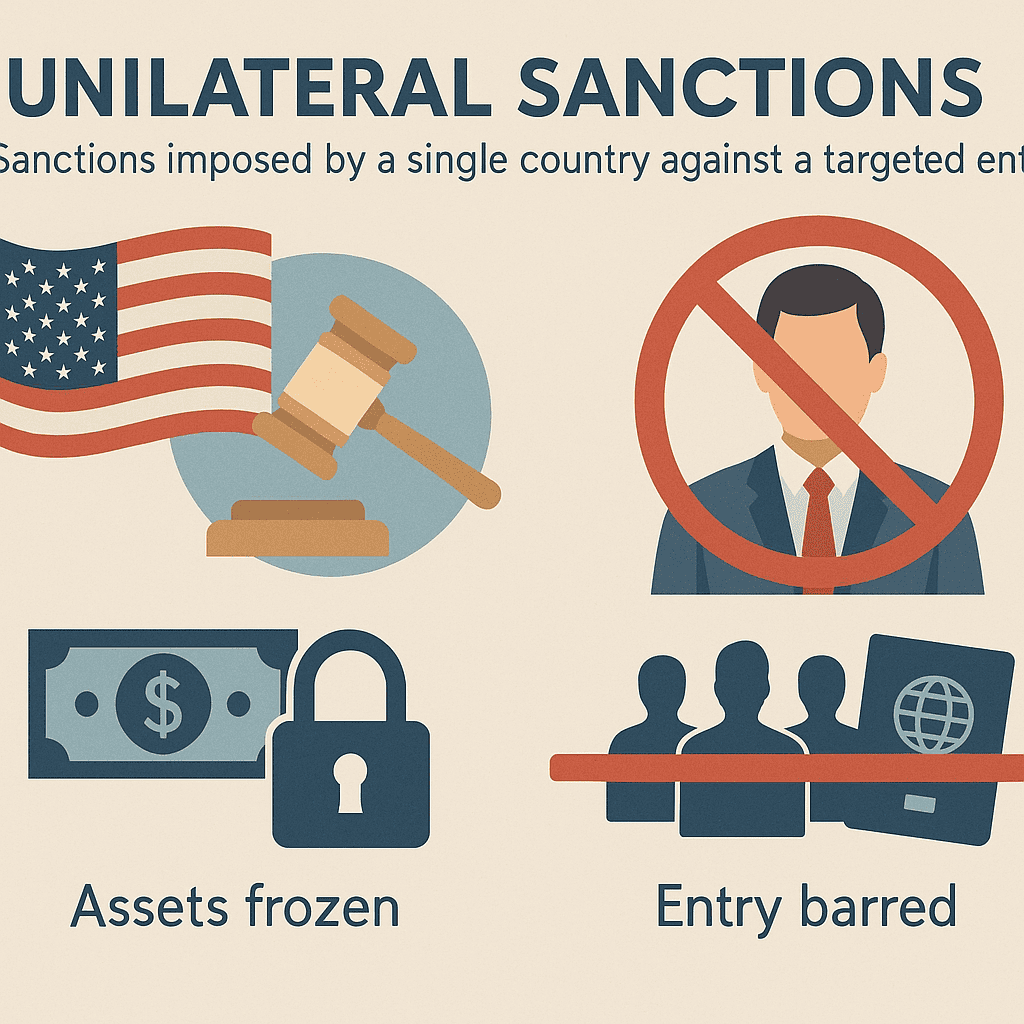
#QuickbiteCompliance day 283 🚨 Unilateral Sanctions: The Double-Edged Sword in Fighting Financial Crime As financial crime fighters, we know unilateral sanctions—imposed by single nations like the U.S., EU, or Australia—are powerful tools to target human rights...
by Tommy Hartono | Jul 28, 2025 | Terms
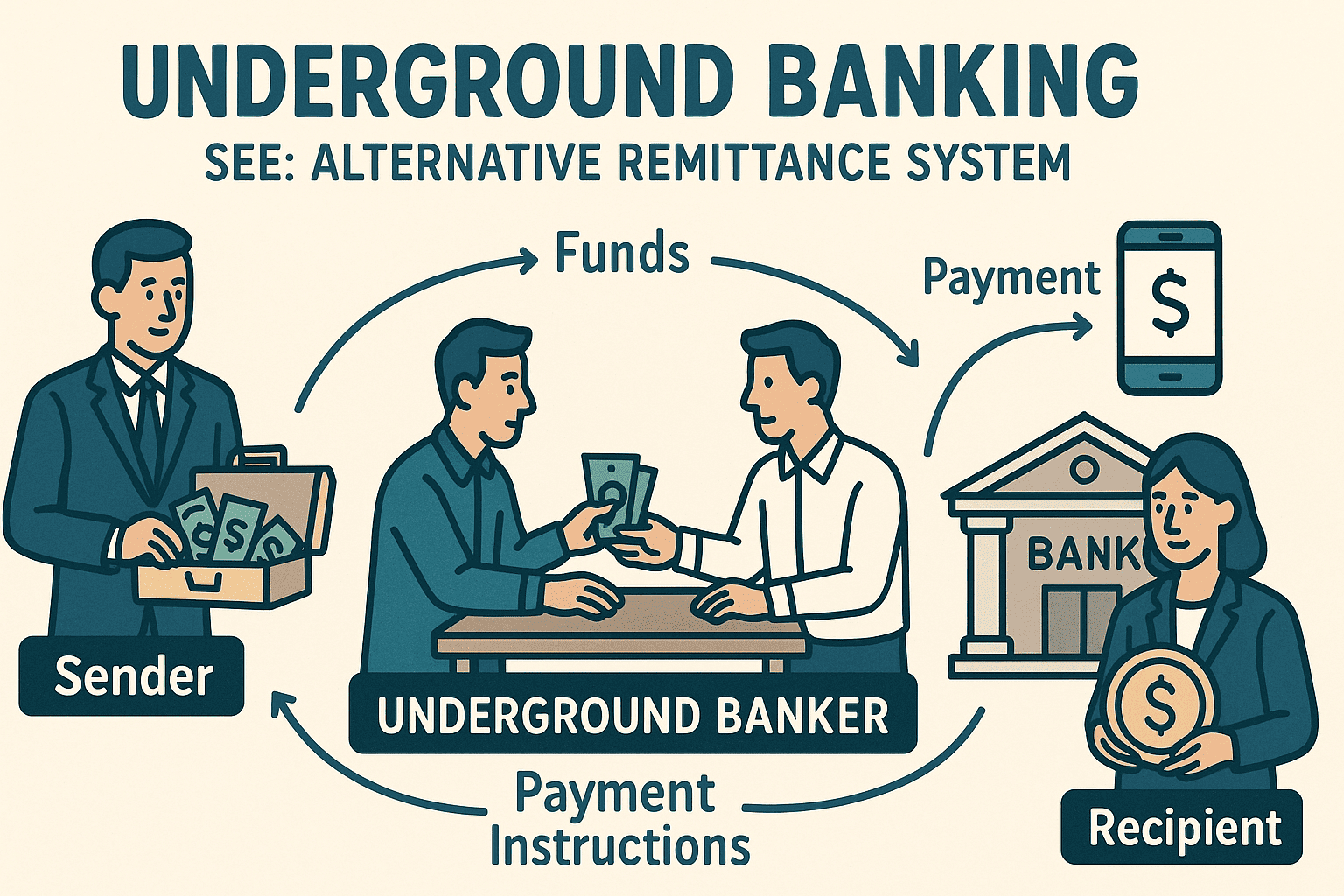
#QuickbiteCompliance day 282 Underground Banking: The Invisible Highway for Financial Crime While traditional banking systems dominate headlines, a parallel financial universe operates in the shadows. Underground Banking—or Alternative Remittance...
by Tommy Hartono | Jul 27, 2025 | Terms
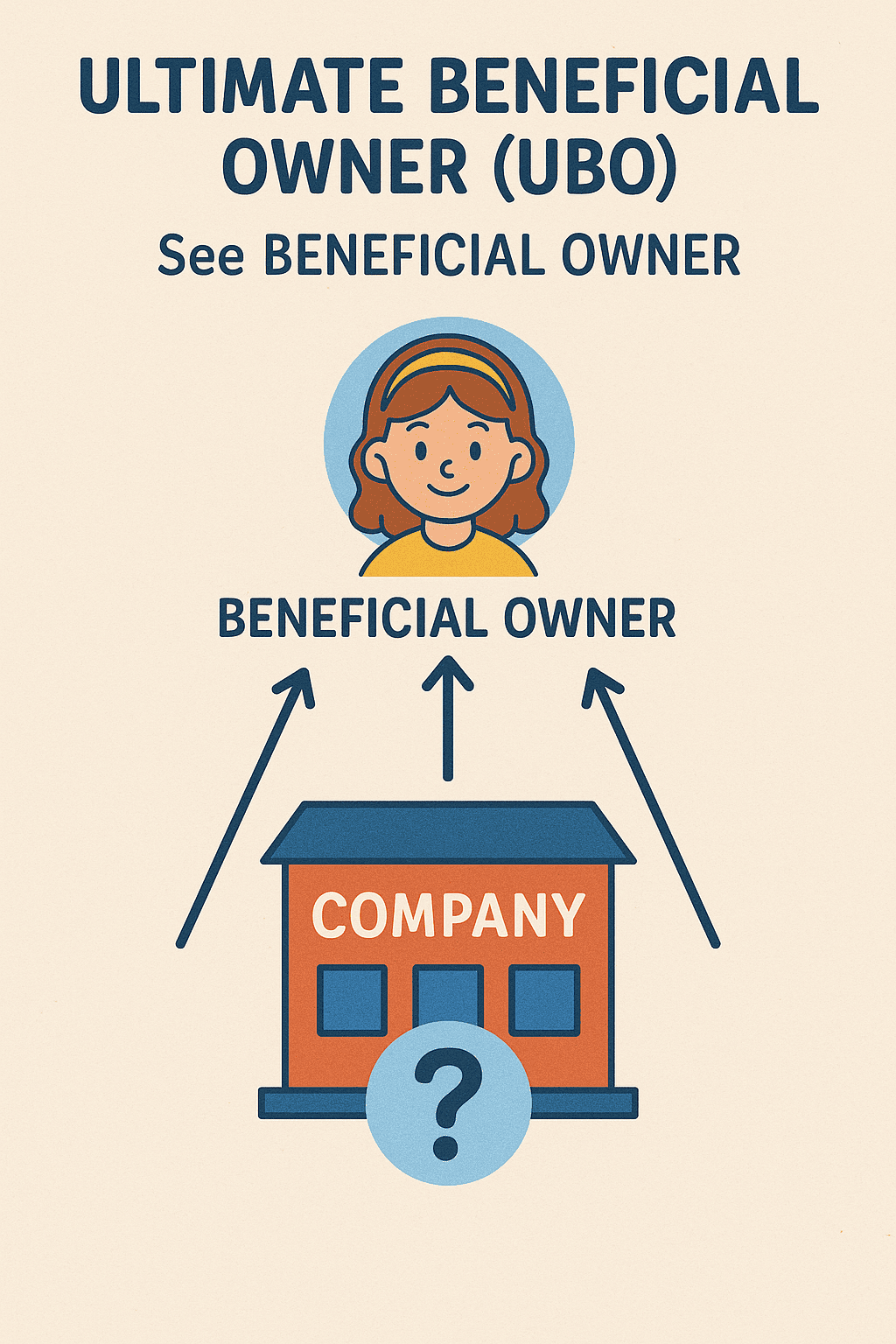
#QuickbiteCompliance day 281 Unmasking the Hidden Puppet Masters: The UBO Story 🔍 Imagine buying a toy from a friend… but the toy actually belongs to their cousin’s neighbor’s dog-walker. Confusing, right? That’s...
by Tommy Hartono | Jul 26, 2025 | Terms
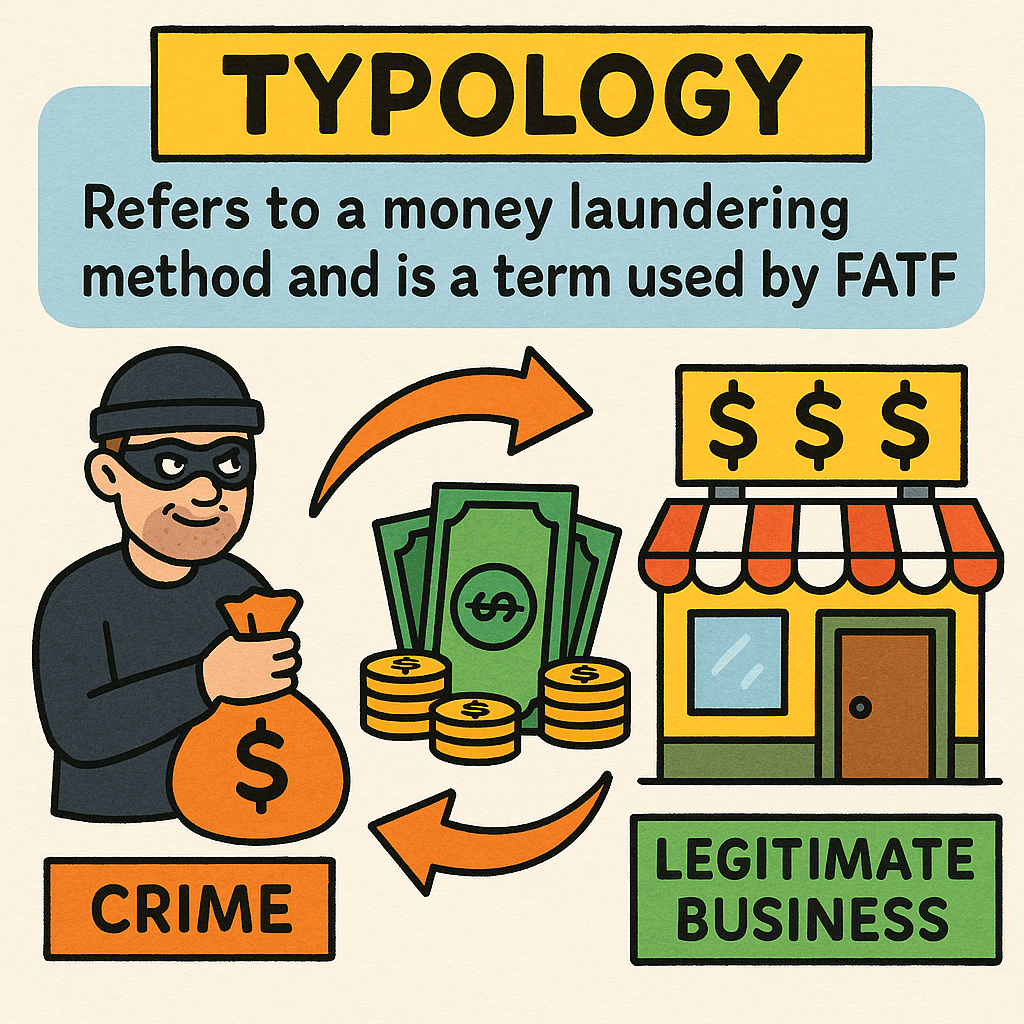
#QuickbiteCompliance day 280 🔍 Catching Bad Guys: What’s a “Typology”? (Hint: It’s Not Dinosaurs!) Imagine a thief steals a cookie 🍪. Instead of eating it whole, they crumble it into tiny pieces, hide crumbs in different jars, swap some for candy 🍬,...







