Category: Terms
-
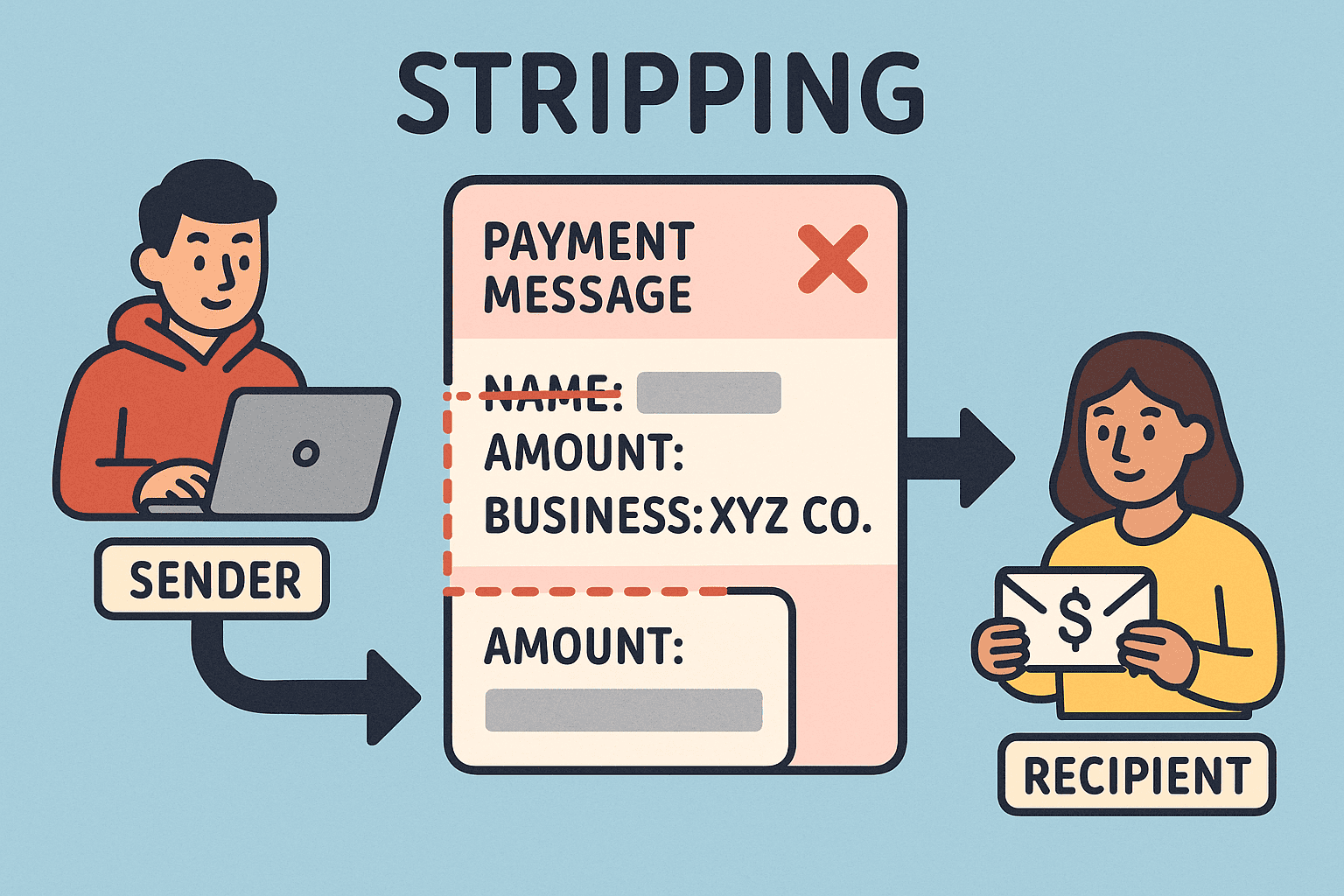
Day 257: Stripping
The “Invisible Money” Trick, known as “Stripping,” allows criminals to obscure the source of illicit funds by altering transaction details. This technique facilitates money laundering, affecting banks globally and increasing costs for consumers. Innovative technologies and collaborative regulations are emerging to combat these practices and enhance financial transparency.
-
Day 256: String Matching
Financial criminals utilize name, number, and code alterations to evade detection, leading to challenges for traditional security systems. Advanced methods like fuzzy matching and analyzing behavioral data enhance fraud detection. By adopting inclusive technologies and shared innovations, we adapt to evolving tactics and improve our defenses against financial crime.
-

Day 255: Strict Liability
Strict liability in sanctions compliance punishes companies for others’ mistakes, allowing criminals to exploit gaps. Tactics include using fake owners, minor invoice errors, and hiding within legitimate businesses to evade fines. To combat this, technology like inclusive regtech can enhance detection of hidden risks, making financial crimes harder to conceal.
-
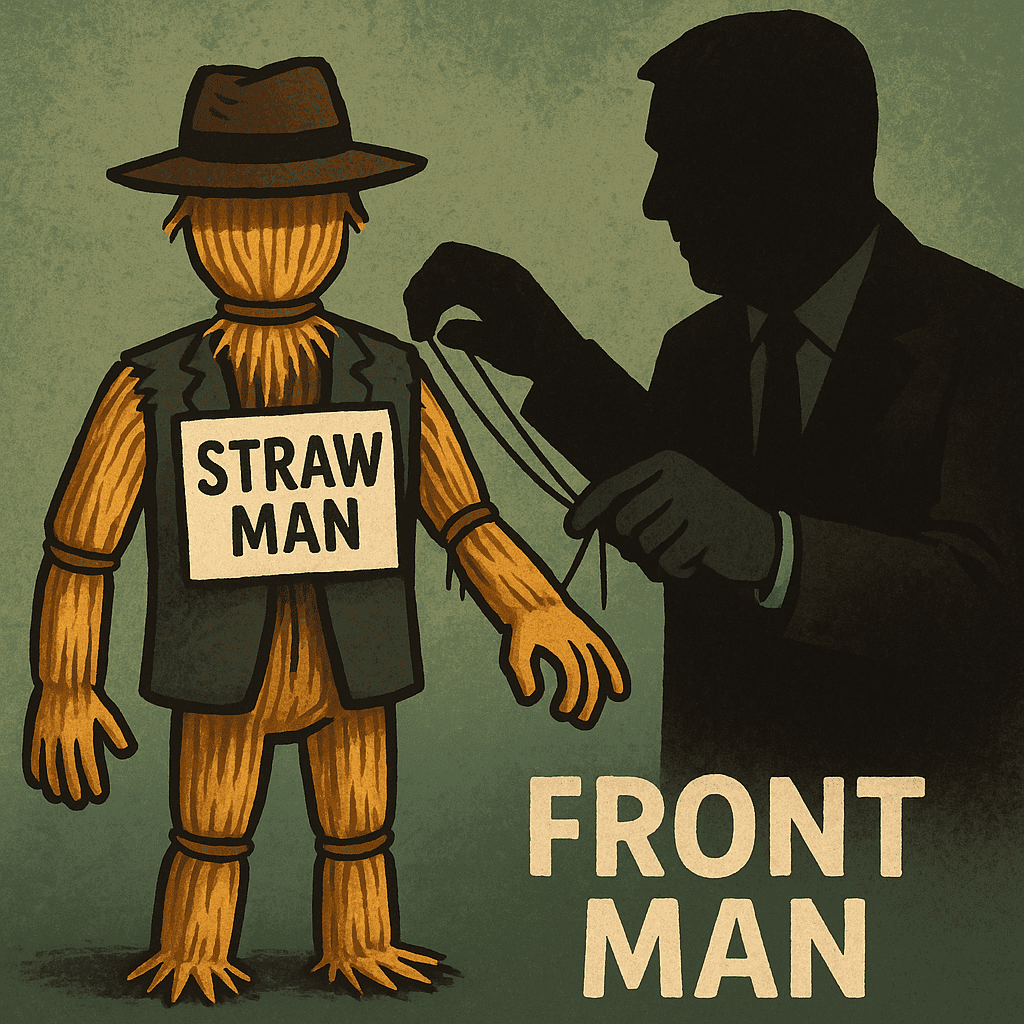
Day 254: Straw Men
#QuickbiteCompliance day 254 🚨 The Puppet Show: How Straw Men Hide Sanctioned Criminals Imagine your friend is banned from the candy store but secretly pays you to buy sweets for them. You’re the “puppet” (aka Straw Man)—acting for someone who’s hiding in the shadows. Here’s how criminals use these puppets to cheat the system: —…
-

Day 253: Sting Operation
#QuickbiteCompliance day 253 🔍 Ever Played “Cops and Robbers”? Real-Life Cops Use “Make-Believe” to Catch Bad Guys! Imagine a police officer dressing up as a watch seller 🕰️, a wedding planner 💒, or even a hacker 💻 to trick criminals into showing their secrets. That’s a “sting operation”! Law enforcement sets up fake businesses (like…
-

Day 252: SDN List
#QuickbiteCompliance day 252 🔍 The SDN List: Your Guide to Fighting Bad Guys Imagine your school has a “no-trade lunchbox” list. If someone steals snacks, they go on the list—and nobody can trade with them. The SDN List works like that for the U.S. government. It’s a list of people, companies, or groups (like terrorists…
-

Day 251: Sources, Secondary
#QuickBiteCompliance day 251 Spotting Financial Crime Red Flags in Plain Sight! Imagine you’re solving a mystery. You have: 🔍 Primary sources: Original “proof” like contracts, ID cards, or bank statements. 📚 Secondary sources: Reports about that proof—like news articles, databases, or corporate registries. Here’s the catch: If these two don’t match? 🚩 That’s a red…
-
Day 250: Sources, Primary
#QuickbiteCompliance day 250 🚨 How Bad Guys Trick the System Using “Primary Sources” (And How We Stop Them) 🚨 Did you know criminals use official-looking lists and documents to hide their dirty money? 🤯 Here’s how it works: – Sanctions lists (like OFAC’s) tell banks who to block—but bad guys create fake companies with similar…
-
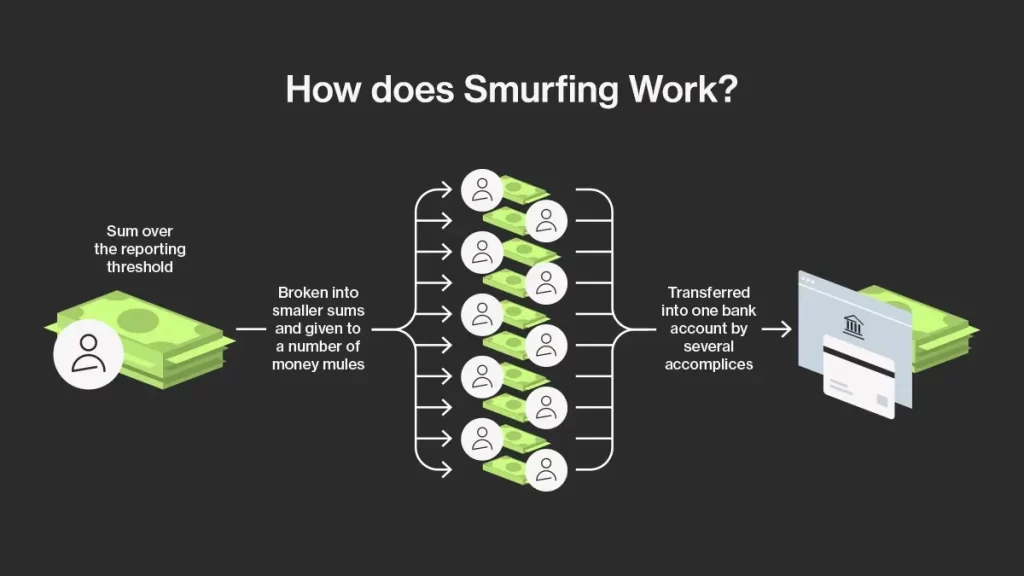
Day 249: Smurfing
#QuickbiteCompliance day 249 🚨 Breaking Down “Smurfing” – The Sneaky Money Laundering Trick! �💵 Ever heard of smurfs? No, not the cute blue cartoon characters—these are the bad guys who help criminals hide dirty money! 💸 How does it work? Imagine a thief has a huge pile of cash from illegal activities. If they deposit…
-
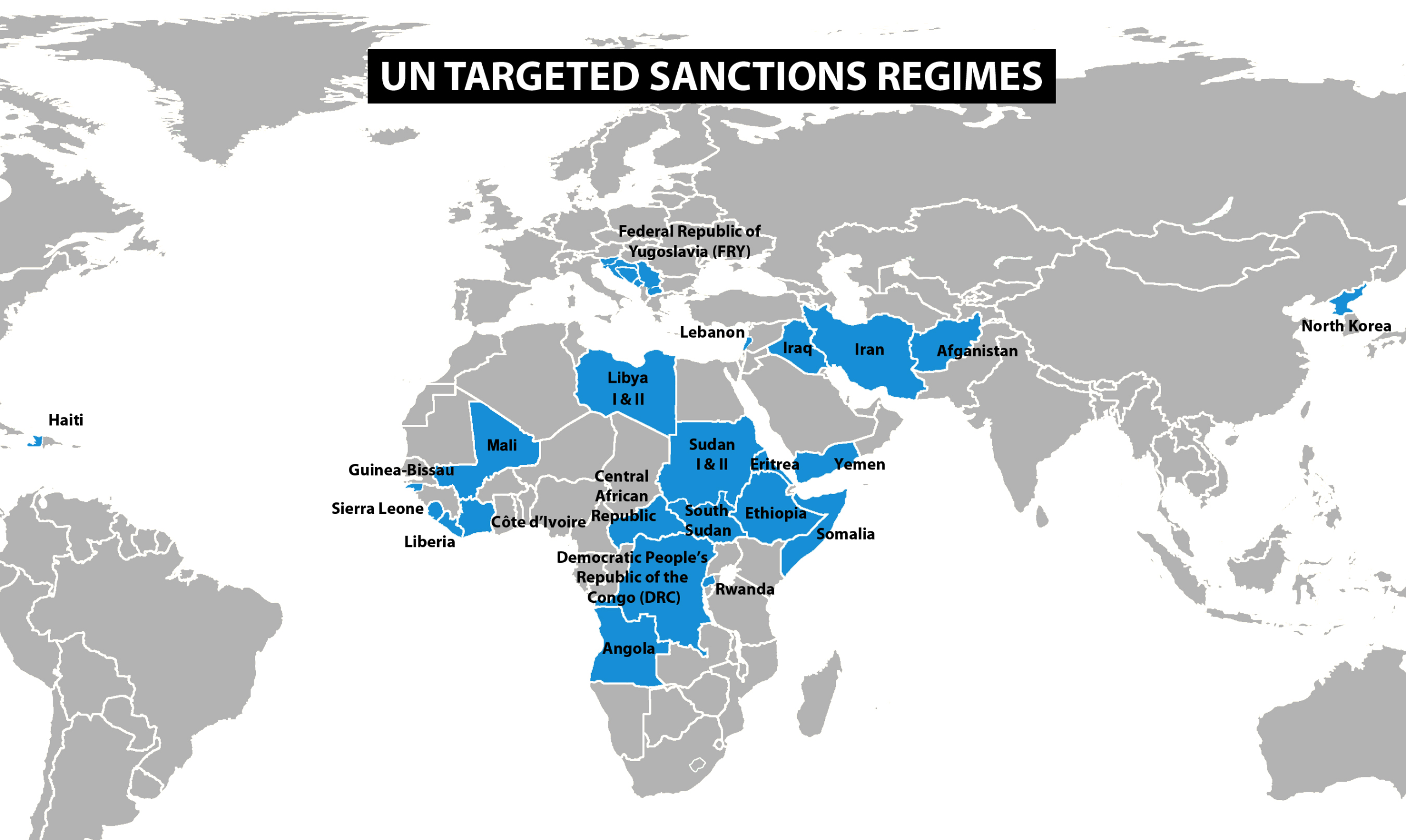
Day 248: Smart Sanctions
#QuickbiteCompliance day 248 🎯 Bullseye Sanctions: Hitting Bad Guys Without Hurting Innocents Imagine trying to stop a school bully by grounding the whole class. That’s what old-school sanctions did—punished entire countries. “Smart sanctions” (or targeted sanctions) are like a laser beam: ➡️ Freeze only the bully’s lunch money (asset freezes). ➡️ Ban only the bully…
